All in Technology simplifies IT for secure, long-term business success.

Network service teams that can design, install, and support technology projects
Develop designs and migration plans that integrates your business with cutting edge technology while supporting current infrastructure
Full Project Management team – allows for clear communication and keeping timelines of projects

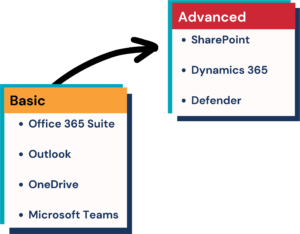 Don’t let outdated tools and disjointed systems hold your business back.
Don’t let outdated tools and disjointed systems hold your business back.
It’s time to unlock the full potential of your organization with Microsoft’s integrated solutions.




Ready to grow your business with seamless and secure IT solutions? Contact All in Technology today.
888-201-5030
855-711-6601
1500 N Grant St, Ste R, Denver, CO 80203
2551 Continental Ct, Ste 1, Green Bay, WI 54311
Please fill out the form below to submit your inquiry. We will review your request and get back to you as soon as possible. Thank you for reaching out to us!